
An optical prism.
There has been a lot of chatter on the Internet since the leak that Prism allowed the NSA to intercept and store everything on the Internet, every where, through the phone companies. Some are shocked. Some have never assumed they had privacy. Some feel violated.
We have been generally lead to believe that if it was behind encryption or a passcode system, that we had the assumption of privacy. But that has not been true for a very long time.
The evidence also shows that the government did not act alone. EFF has obtained whistleblower evidence [PDF] from former AT&T technician Mark Klein showing that AT&T is cooperating with the illegal surveillance. The undisputed documents show that AT&T installed a fiber optic splitter at its facility at 611 Folsom Street in San Francisco that makes copies of all emails web browsing and other Internet traffic to and from AT&T customers and provides those copies to the NSA. This copying includes both domestic and international Internet activities of AT&T customers. As one expert observed “this isn’t a wiretap, it’s a country-tap.”
There are several ongoing Court cases being pursued by Electronic Frontier Foundation concerning the total disregard of privacy rights by internet service providers [ISP]:
Currently, EFF is representing victims of the illegal surveillance program in Jewel v. NSA, a lawsuit filed in September 2008 seeking to stop the warrantless wiretapping and hold the government and government officials officials behind the program accountable.
Previously, in Hepting v. AT&T, EFF filed the first case against a cooperating telecom for violating its customers’ privacy. After Congress expressly intervened in the FISA Amendments Act to allow the Executive to require dismissal of the case, the case was ultimately dismissed by the US Supreme Court.
Other ongoing cases arising from the warrantless wiretapping are:
Amnesty International v. Clapper
And in light of the leaks on 5 June 2013:
In light of the confirmation of NSA surveillance of millions of Americans’ communications records, and especially the decision by the government to declassify and publicly release descriptions of the program, the government today asked the courts handling two EFF surveillance cases for some additional time to consider their options.
The first notice comes in EFF’s Jewel v. NSA case (along with a companion case called Shubert v. Obama), which seeks to stop the spying and obtain an injunction prohibiting the mass collection of communications records by the government. While the Guardian importantly confirmed this with government documents on Wednesday and Thursday, we’ve been arguing for seven years in court that the NSA has been conducting the same type of dragnet surveillance. In the government’s motion, they ask the court to hold the case in abeyance and that the parties file a status report by July 12, 2013.
The second notice comes in EFF’s Freedom of Information Act (FOIA) case seeking the DOJ’s secret legal interpretations of Section 215 of the Patriot Act (50 U.S.C. section 1861), which was the statute cited in the leaked secret court order aimed at Verizon. Sen. Wyden and Sen. Udall have long said publicly that the American public would be “shocked” to know how the government is interpreting this statute. The leaked court order gives us an idea of what they were talking about. The government seeks a status report within 30 days of today, June 7, 2013.
In both of these cases, the government has long claimed broad secrecy.
Electronic Freedom Foundation went as far as calling for a new Church Committee:
[The National Security Agency’s] capability at any time could be turned around on the American people, and no American would have any privacy left, such is the capability to monitor everything: telephone conversations, telegrams, it doesn’t matter. There would be no place to hide.” —Senator Frank Church, 1975
Following on the heels of the Guardian reporting that the NSA is collecting all US call data records of Verizon customers, the Guardian and Washington Post yesterday reported that nine of the biggest Internet companies, including Facebook, Google, Yahoo, and Microsoft, are also working with the government in a vast spying program, where a massive amount of online data flows to the NSA, all in secret.
While I agree that Congressional oversight is clearly lacking, this current Congress has shown an overwhelming desire to throw Civil Rights under the bus–approving Indefinite Detention of American Citizens on American soil being the most flagrant. Since 9/11, Congress has been a rubber stamp for the Administration when it comes to the War on Terror. And it didn’t matter whether it was George W. Bush or Barack Obama. We have the separation of powers for a reason–Congress in 2 Houses is meant to be a brake on the power of the Administration.
We keep going back to the Patriot Act as the source of our loss of privacy, our loss of rights, our loss of freedom. There was only one Senator who voted against it in 2001: Russ Feingold. And here is his speech via CSPAN:
Russ Feingold’s speech against the Patriot Act in 2001.
We do have to make choices. But Feingold understood back then that the choice isn’t that simple:
Some have said rather cavalierly that in these difficult times we must accept some reduction in our civil liberties in order to be secure.
Of course, there is no doubt that if we lived in a police state, it would be easier to catch terrorists. If we lived in a country that allowed the police to search your home at any time for any reason; if we lived in a country that allowed the government to open your mail, eavesdrop on your phone conversations, or intercept your email communications; if we lived in a country that allowed the government to hold people in jail indefinitely based on what they write or think, or based on mere suspicion that they are up to no good, then the government would no doubt discover and arrest more terrorists.
But that probably would not be a country in which we would want to live. And that would not be a country for which we could, in good conscience, ask our young people to fight and die. In short, that would not be America.
Preserving our freedom is one of the main reasons that we are now engaged in this new war on terrorism. We will lose that war without firing a shot if we sacrifice the liberties of the American people.
That is exactly the argument civil libertarians need to be making.
And a Police State has been the result of the Patriot Act. An overwhelming militarization of the local police, some locales even have tanks now. Citizens are murdered by the police for totally unknown reasons, with impunity. New York State just made it a felony to bother a police officer. We have the highest incarceration rates in our history, since 2002 the highest in the world, and for-profit-private prisons require 90% occupancy as part of their contracts with the individual States.
Dealing With ‘Root Causes’ To Tackle Incarceration Rates — March 02, 2013
So, we have found the root cause of the Police State to be the Patriot Act. How did the Federal government take control of the Internet?

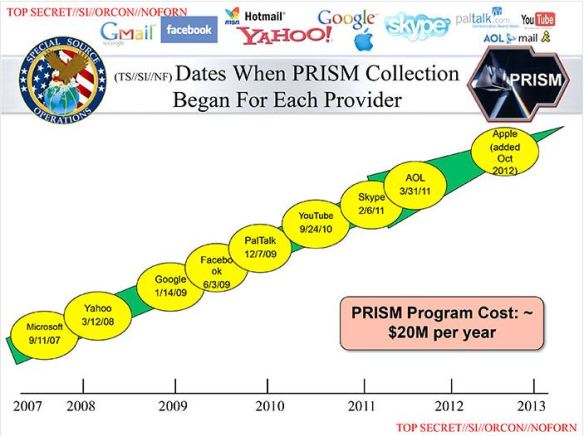
Dates when PRISM collection began by each provider. Via: washingtonpost.com
Does that mean we were all safe before 2007? Hardly. FaceBook was developed using funding from DARPA–a CIA investment fund. In fact, the CIA through DARPA actually developed the Arpanet, the precurser to today’s Internet. Which actually supports those who view privacy on the Internet as non-existent from the beginning. But the CIA doesn’t like to share with the NSA, Patriot Act or not.
The tiny $20 million program budget listed in the leaked documents speaks to just how unstoppable PRISM-like programs are; judging from the limited evidence we have, this was neither a major technological undertaking for the government ($20 million would get the NSA nowhere on a true mass-monitoring project unless it had help from the companies it’s monitoring) nor a public fight. Google has raised a vague stink; Twitter, which was not listed but hasn’t responded to the reports yet, has made a point of fighting the government in a few high profile cases. But if the tech giants wanted to put up an all-or-nothing fight, it would be in their interest to make it a public one. In other words, we would know.
The companies that have responded to requests for comment have so far offered varied, incomplete and very carefully worded denials, denying specific details about PRISM rather than offering full-throated denunciations of secret government cooperation. Even the most adamant denials suggest greater cooperation with the government than most people are aware of.
And a couple of them have done denials:
“Google cares deeply about the security of our users’ data. We disclose user data to government in accordance with the law, and we review all such requests carefully. From time to time, people allege that we have created a government ‘back door’ into our systems, but Google does not have a ‘back door’ for the government to access private user data.”
[FYI — ” back door” is done without the company’s knowledge. PRISM was the law, such as it was. So technically, this may be the absolute letter-of-the-law truth.]
Chiefsecurity officer Joe Sullivan told Forbes :
“Protecting the privacy of our users and their data is a top priority for Facebook. We do not provide any government organization with direct access to Facebook servers. When Facebook is asked for data or information about specific individuals, we carefully scrutinize any such request for compliance with all applicable laws, and provide information only to the extent required by law.”
Here, again “only to the extent required by law.” And if there was a gag order on the request, as is common practice?
First, it turns out Facebook and Google weren’t lying. The government does not have “direct access” to their servers. But they did make something special for the NSA to make obtaining the specially requested information as easy as a ransom hand-off. Per Miller:
In at least two cases, at Google and Facebook, one of the plans discussed was to build separate, secure portals, like a digital version of the secure physical rooms that have long existed for classified information, in some instances on company servers. Through these online rooms, the government would request data, companies would deposit it and the government would retrieve it, people briefed on the discussions said.
. . . How other tech companies linked to PRISM ended up cooperating is unclear at this time. Twitter is only one who bristled at the government’s request to make the handing-over of information easier.
. . . These tech companies have no choice but to fork over the information when the NSA came calling. “The companies were legally required to share the data under the Foreign Intelligence Surveillance Act,” Miller reminds us. But building the special secure server used for dumping information for the NSA was going above and beyond the legal call of duty.
And the Director of National Intelligence also felt he had to make a statement:
The highest priority of the Intelligence Community is to work within the constraints of law to collect, analyze and understand information related to potential threats to our national security.
The unauthorized disclosure of a top secret U.S. court document threatens potentially long-lasting and irreversible harm to our ability to identify and respond to the many threats facing our nation.
The article omits key information regarding how a classified intelligence collection program is used to prevent terrorist attacks and the numerous safeguards that protect privacy and civil liberties.
I believe it is important for the American people to understand the limits of this targeted counterterrorism program and the principles that govern its use. In order to provide a more thorough understanding of the program, I have directed that certain information related to the “business records” provision of the Foreign Intelligence Surveillance Act be declassified and immediately released to the public.
It must BE really important for the Head Spook to direct releases. But he doesn’t say that he’s sharing the information further abroad.
London’s Guardian newspaper reported Friday that GCHQ, Britain’s equivalent of the NSA, also has been secretly gathering intelligence from the same internet companies through an operation set up by the NSA.
. . . PRISM was launched from the ashes of President George W. Bush’s secret program of warrantless domestic surveillance in 2007, after news media disclosures, lawsuits and the Foreign Intelligence Surveillance Court forced the president to look for new authority.
Congress obliged with the Protect America Act in 2007 and the FISA Amendments Act of 2008, which immunized private companies that cooperated voluntarily with U.S. intelligence collection. PRISM recruited its first partner, Microsoft, and began six years of rapidly growing data collection beneath the surface of a roiling national debate on surveillance and privacy. Late last year, when critics in Congress sought changes in the FISA Amendments Act, the only lawmakers who knew about PRISM were bound by oaths of office to hold their tongues.
The court-approved program is focused on foreign communications traffic, which often flows through U.S. servers even when sent from one overseas location to another. Between 2004 and 2007, Bush administration lawyers persuaded federal FISA judges to issue surveillance orders in a fundamentally new form. Until then the government had to show probable cause that a particular “target” and “facility” were both connected to terrorism or espionage.
In four new orders, which remain classified, the court defined massive data sets as “facilities” and agreed to certify periodically that the government had reasonable procedures in place to minimize collection of “U.S. persons” data without a warrant.
And where does the NSA store all this data?
Under construction by contractors with top-secret clearances, the blandly named Utah Data Center is being built for the National Security Agency. A project of immense secrecy, it is the final piece in a complex puzzle assembled over the past decade. Its purpose: to intercept, decipher, analyze, and store vast swaths of the world’s communications as they zap down from satellites and zip through the underground and undersea cables of international, foreign, and domestic networks. The heavily fortified $2 billion center should be up and running in September 2013. Flowing through its servers and routers and stored in near-bottomless databases will be all forms of communication, including the complete contents of private emails, cell phone calls, and Google searches, as well as all sorts of personal data trails—parking receipts, travel itineraries, bookstore purchases, and other digital “pocket litter.” It is, in some measure, the realization of the “total information awareness” program created during the first term of the Bush administration—an effort that was killed by Congress in 2003 after it caused an outcry over its potential for invading Americans’ privacy.
. . .Given the facility’s scale and the fact that a terabyte of data can now be stored on a flash drive the size of a man’s pinky, the potential amount of information that could be housed in Bluffdale is truly staggering. But so is the exponential growth in the amount of intelligence data being produced every day by the eavesdropping sensors of the NSA and other intelligence agencies. As a result of this “expanding array of theater airborne and other sensor networks,” as a 2007 Department of Defense report puts it, the Pentagon is attempting to expand its worldwide communications network, known as the Global Information Grid, to handle yottabytes (1024 bytes) of data. (A yottabyte is a septillion bytes—so large that no one has yet coined a term for the next higher magnitude.)
It needs that capacity because, according to a recent report by Cisco, global Internet traffic will quadruple from 2010 to 2015, reaching 966 exabytes per year. (A million exabytes equal a yottabyte.) In terms of scale, Eric Schmidt, Google’s former CEO, once estimated that the total of all human knowledge created from the dawn of man to 2003 totaled 5 exabytes. And the data flow shows no sign of slowing. In 2011 more than 2 billion of the world’s 6.9 billion people were connected to the Internet. By 2015, market research firm IDC estimates, there will be 2.7 billion users. Thus, the NSA’s need for a 1-million-square-foot data storehouse. Should the agency ever fill the Utah center with a yottabyte of information, it would be equal to about 500 quintillion (500,000,000,000,000,000,000) pages of text.
Apparently, these people never listened to the moral of the film “Colossus, the Forbin Project“. But this is more data that those nine tech companies and assorted phone companies could come up with. Where are they getting the rest of the data? TrapWire is one place.
“The genesis of our company started with a project initiated in the wake of the September 11th terrorist attacks,” TrapWire said. “The objective of that project was to develop a capability that would prevent such attacks from occurring in the future. This project evolved into our flagship product, TrapWire, and its related methodologies and supporting capabilities.”
The released emails, however, were surprising in that they discuss a far-reaching surveillance effort about which many Americans are likely unaware.
RT.com said Trap Wire was developed by Abraxas, whose founder, Richard Helms, told The Entrepreneur Center in 2005 that his company’s technology “can collect information about people and vehicles that is more accurate than facial recognition, draw patterns, and do threat assessments of areas that may be under observation from terrorists.”
Sophos analyst Carole Theriault said in a Monday blog post that she didn’t “think anyone is really surprised that the governments and authorities are quietly using the latest technology to monitor the activities of its people, saying that they are doing this for our general safety.”
“The question we all need to ask ourselves is this: What do we value more – privacy or state security?” Theriault wrote. “Sadly, it seems that we cannot get both.”
And what has happened to the young man who brought us the knowledge of TrapWire?
Jeremy Hammond on Tuesday pleaded guilty to hacking intelligence firm Stratfor to expose millions of emails, with some of the more revealing ones later published by WikiLeaks.
The Illinois native faces up to 10 years in prison when he is sentenced Sept. 6. As part of his plea deal, Hammond, who was involved with Anonymous and offshoot LulzSec, accepted responsibility for infiltrating a number of other intelligence-related sites, including including equipment suppliers and police agencies. He had been publicly accused of illegally accessing the Arizona Department of Public Safety.
In a Tuesday statement posted on his support website, FreeJeremy.net, Hammond said that by pleading guilty, he is protected from being prosecuted for the other offenses. Hammond has been held without bail in a New York jail since March 2012, often placed in solitary confinement and denied visitors.
“[E]ven if I was found not guilty at trial [in New York], the government claimed that there were eight other outstanding indictments against me from jurisdictions scattered throughout the country” he wrote. “If I had won this trial, I would likely have been shipped across the country to face new but similar charges in a different district. The process might have repeated indefinitely.”
Hammond also stated that he was proud he shed light on the secret dealings of Stratfor, which serves major corporate and government agency clients. According to a Rolling Stone article published in December, the emails referenced “nefarious and clandestine activities – from the U.S. government’s monitoring of the Occupy movement to Stratfor’s own role in compiling data on a variety of activist movements, including PETA, Wikileaks and even Anonymous itself.”
And:
Earlier this week, The Associated Press stunningly revealed that the U.S. Department of Justice secretly obtained “records for more than 20 separate telephone lines assigned to the AP and its journalists” covering “a full two-month period in early 2012.” Presumably the feds were interested in finding out who had leaked to the AP information about a foiled al-Qaeda plot in Yemen, and Attorney General Eric Holder justified the snooping in the name of national security, an argument that, as the days pass, is growing increasingly dubious.
. . . The AP probe and LulzSec punishments may not, on the surface, appear connected. But they are, especially when one considers the case of Jeremy Hammond, the accused Anonymous and LulzSec-linked hacktivist who is charged with looting the computer systems belonging to the Arizona Department of Public Safety (allegedly done to protest tough immigration laws) and at HBGary Federal and global intelligence firm Stratfor (allegedly done to expose the inner workings of the so-called intelligence industrial complex). The Stratfor hack resulted in millions of emails being unearthed and, according to Rolling Stone, “focused worldwide attention on the murky world of private intelligence after Anonymous provided the firm’s emails to WikiLeaks, which has been posting them ever since.”
. . . It’s clear that the United States wants to make an example of Hammond, and by throwing the proverbial book at him and essentially declaring him an enemy of the state, even before he stands trial, federal prosecutors are fully aware that this will discourage other people from engaging in similar acts that seek to expose government or corporate corruption and impropriety. The same applies to what the DoJ has done to the AP. In many ways, Hammond really is no different than the person or persons who tipped off the news agency about the counter-terrorism operation in Yemen. Or any whistleblower or press leaker for that matter. Hence, they all face similar treatment.
Although President Obama pledged to maintain the “most transparent administration” in history, his actions have proven otherwise. The events of this week is further proof that the U.S government — and the corporations for which it looks out — is more interested than ever in preserving its cloak of national security secrecy. And if that means instituting press or source intimidation, or waging aggressive prosecutions against activists…well, you might want to get used to it.
What do I think of it all? I think the Patriot Act should be repealed. I think FISA should be repealed. I think the entire subject of what is, or is not, acceptable invasion of privacy vis-a-vis national security should be a matter of national, even international, public debate.
And in the meantime, assume Big Brother is watching and listening. Welcome to 1984.


Hello. excellent job. I did not expect this. This is a impressive story. Thanks!
I significantly appreciate your posts. Many thanks